Delving into the world of Secure remote management tools, this introduction aims to pique the interest of readers by highlighting the importance of secure tools in today's business landscape.
Exploring the features and best practices surrounding secure remote management tools, this guide provides valuable insights for businesses seeking to enhance their security measures.
Importance of Secure Remote Management Tools
Secure remote management tools play a critical role in the operations of modern businesses, providing a secure way to remotely access and manage IT systems, networks, and devices. These tools are essential for ensuring the efficiency, productivity, and security of a company's digital infrastructure.
Potential Risks of Using Insecure Remote Management Tools
- Unauthorized Access: Insecure remote management tools can be vulnerable to cyberattacks, allowing malicious actors to gain unauthorized access to sensitive data or systems.
- Data Breaches: Using insecure tools increases the risk of data breaches, potentially exposing confidential information to cybercriminals.
- Malware Infections: Without proper security measures, remote management tools can be targeted by malware, leading to compromised systems and networks.
Impact of a Security Breach Due to Inadequate Remote Management Tools
- Financial Loss: A security breach resulting from inadequate remote management tools can lead to financial losses due to data theft, system downtime, and costly recovery efforts.
- Reputational Damage: A breach can tarnish a company's reputation, eroding customer trust and loyalty, and negatively impacting its brand image.
- Legal Consequences: Inadequate security measures can result in legal repercussions, such as regulatory fines and lawsuits, further adding to the financial burden.
Features of Effective Secure Remote Management Tools
Effective secure remote management tools have a variety of features that contribute to their ability to keep sensitive information safe and secure. These key features play a crucial role in maintaining the integrity of remote management systems and ensuring that unauthorized access is prevented.
Encryption for Data Security
Encryption is a fundamental feature of secure remote management tools as it helps to protect data as it is transmitted between devices. By encrypting data, information is converted into a code that can only be deciphered by authorized users with the appropriate decryption key.
This ensures that sensitive data remains confidential and secure, even if intercepted by cyber attackers.
Multi-Factor Authentication
Multi-factor authentication adds an extra layer of security to remote management tools by requiring users to provide multiple forms of verification before accessing the system. This typically includes something the user knows (like a password), something they have (such as a security token), and something they are (like a fingerprint or facial recognition).
By combining these different authentication factors, multi-factor authentication significantly reduces the risk of unauthorized access and enhances overall security.
Best Practices for Implementing Secure Remote Management Tools
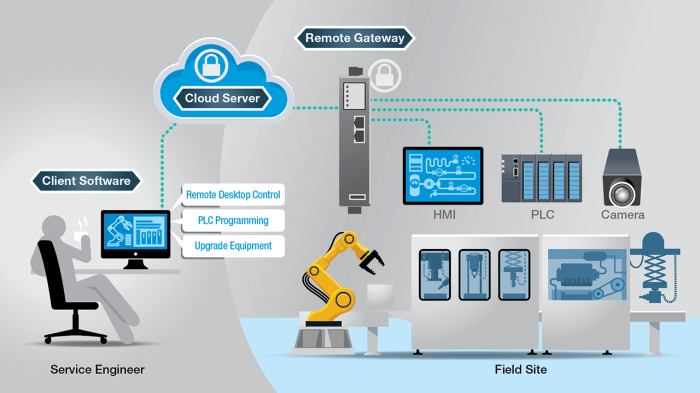
When it comes to implementing secure remote management tools, following best practices is crucial to ensure the safety and efficiency of your remote operations. Below are some steps and tips to help you set up and maintain secure remote management tools effectively.
Step-by-Step Guide to Set Up Secure Remote Management Tools:
- Choose a reputable remote management tool that offers robust security features.
- Ensure that the tool uses encryption to protect data transmission.
- Set up strong authentication methods, such as multi-factor authentication, to control access to the tool.
- Configure access controls to restrict permissions based on user roles and responsibilities.
- Regularly update the remote management tool and keep it patched to address any security vulnerabilities.
Importance of Regular Software Updates for Maintaining Security:
Regular software updates are essential for maintaining the security of remote management tools. By updating the tool regularly, you ensure that any known security vulnerabilities are patched, reducing the risk of unauthorized access or data breaches. It is important to stay informed about the latest updates and to apply them promptly to keep your remote management tool secure
Tips for Training Employees to Use Remote Management Tools Securely:
- Provide comprehensive training on the proper use of the remote management tool, including security best practices.
- Emphasize the importance of maintaining strong passwords and using authentication methods effectively.
- Regularly conduct security awareness training to keep employees informed about the latest threats and security practices.
- Encourage employees to report any suspicious activity or security concerns related to the remote management tool.
Comparison of Different Secure Remote Management Tools
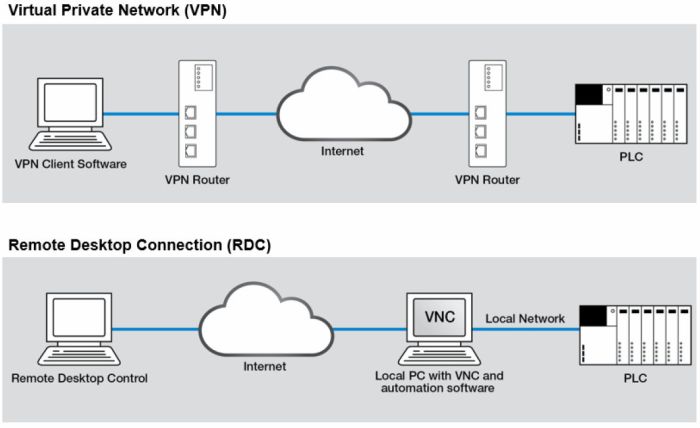
When it comes to secure remote management tools, there are several popular options available in the market. These tools vary in terms of features, scalability, user interface, and ease of use. Let's compare and contrast some of the leading secure remote management tools to help you make an informed decision for your business.
TeamViewer
TeamViewer is a widely used remote management tool that offers a range of features such as remote desktop access, file transfer, and collaboration tools. It is known for its ease of use and cross-platform compatibility, making it a popular choice for businesses of all sizes.
However, TeamViewer can be expensive for larger organizations with multiple users.
Remote Desktop Manager
Remote Desktop Manager is another secure remote management tool that provides centralized access to remote connections, passwords, and credentials. It offers strong security features and supports a wide range of protocols. This tool is highly scalable and suitable for businesses of all sizes.
However, the user interface may not be as intuitive as some other tools.
LogMeIn Pro
LogMeIn Pro is a remote management tool that focuses on ease of use and simplicity. It offers features such as remote desktop access, file sharing, and remote printing. LogMeIn Pro is known for its user-friendly interface and quick setup process.
However, it may lack some advanced features compared to other tools.
Splashtop Business Access
Splashtop Business Access is a remote management tool that emphasizes fast remote access to computers and virtual desktops. It offers high-performance remote connections and strong security measures. Splashtop Business Access is suitable for businesses looking for a reliable and efficient remote management solution.
However, it may not have as many collaboration features as other tools.Overall, the choice of secure remote management tool will depend on your specific business needs, budget, and preferences. It's essential to evaluate the scalability, user interface, and feature set of each tool to determine which one best suits your requirements.
Last Recap

In conclusion, Secure remote management tools are indispensable for safeguarding businesses against potential risks. By understanding the key features, best practices, and comparisons of various tools, organizations can better protect their data and operations in an increasingly digital world.
Detailed FAQs
How do secure remote management tools benefit businesses?
Secure remote management tools help businesses protect sensitive data, enhance operational efficiency, and mitigate the risks of cyber threats.
What role does encryption play in secure remote management tools?
Encryption ensures that data transmitted through remote management tools is secure and protected from unauthorized access.
Why is multi-factor authentication important for secure remote management?
Multi-factor authentication adds an extra layer of security by requiring users to provide multiple forms of verification before accessing remote management tools.